Building Secure Software: Best Practices and Techniques

In the present interconnected advanced scene, programming applications have turned into a basic piece of our lives, working with everything from correspondence to monetary exchanges. As programming keeps on forming our reality, guaranteeing its security has never been more basic. Digital dangers are consistently advancing, and engineers should embrace proactive measures to construct secure programming that shields client information and supports against possible breaks. This blog gives a top-to-bottom investigation of the prescribed procedures and strategies fundamental for creating secure programming.
- Understanding Software Security
Before diving into best practices, understanding the meaning of programming security is essential. Programming security includes shielding applications and information from unapproved access, alteration, or annihilation. A thorough way to deal with security incorporates distinguishing likely weaknesses, evaluating dangers, and carrying out suitable measures to relieve chances.
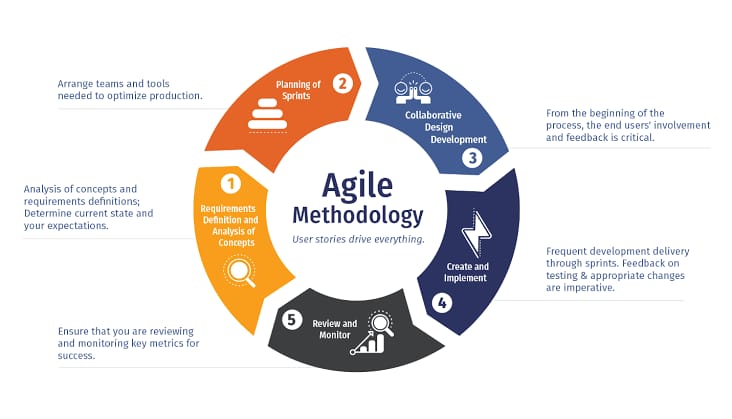
- Secure Software Development Lifecycle (SDLC)
Implementing security from the inception of software development is essential. The Safe SDLC incorporates security rehearses into each period of advancement, including arranging, planning, coding, testing, and arrangement. Taking on this approach guarantees that security isn't a reconsideration yet a key part of the product's engineering.
- Secure Coding Practices
Building safe software starts with writing secure code. To avoid widespread vulnerabilities like SQL injection, cross-site scripting (XSS), and buffer overflows, developers must follow safe coding practices such as input validation, output encoding, and parameterized queries.
- Regular Security Testing
Periodic security testing is vital to identify and address potential vulnerabilities. Techniques like penetration testing and code reviews help evaluate the effectiveness of implemented security measures and discover any weaknesses that hackers could exploit.
- Data Encryption
Encrypting sensitive data ensures that even if unauthorized parties gain access to the information, it remains indecipherable. Properly implemented encryption mechanisms protect data both in transit and at rest, enhancing the overall security posture of the application.
- Authentication and Authorization
Implementing robust authentication mechanisms is essential for controlling access to the software. Multifaceted confirmation (MFA) adds another layer of safety, decreasing the gamble of unapproved access. Appropriate approval guarantees that clients can get to the functionalities they are allowed to utilize.
- Input Validation and Sanitization
Invalidated user inputs can lead to severe security vulnerabilities. Implementing thorough input validation and data sanitization prevents attacks like SQL injection and helps maintain data integrity.
- Regular Updates and Patch Management
Software security is an ongoing process. Keeping the software up to date with the latest security patches and updates is crucial for addressing newly discovered vulnerabilities and strengthening the application's resilience against emerging threats.
- Secure Software Architecture
Designing a secure architecture is fundamental to building secure software. Employing secure design patterns and following the principle of least privilege helps create a robust foundation that is less susceptible to exploitation.
- Employee Training and Awareness
Human error remains one of the leading causes of security breaches. Training developers and other staff members on security best practices and fostering security awareness throughout the organization are essential components of a comprehensive security strategy.
- Secure Third-Party Components
Incorporating third-party libraries and components in software development can be convenient, but it also introduces potential risks. Regularly monitoring and updating these components to address security vulnerabilities is vital to maintaining a secure application.
- Secure APIs
If your software utilizes APIs, ensure that they are designed with security in mind. Implement secure authentication and authorization mechanisms to prevent unauthorized access and data leakage through API endpoints.
- Incident Response Plan
No matter how well-prepared you are, security incidents can still occur. Having an obvious occurrence reaction plan set up permits you to answer speedily and proficiently to any security breaks, limiting their effect on your product and clients.
Building secure programming requires a proactive methodology, with security coordinated into each step of the improvement interaction. By following accepted procedures and utilizing proper strategies, designers can essentially decrease the gamble of weaknesses and digital assaults. Focusing on programming security safeguards client information and protection as well as improves the standing and reliability of the application, eventually prompting long haul progress in the present network safety scene.
In the present computerized age, where programming is at the core of pretty much every part of our lives, building secure programming has turned into a basis for people and associations. In this blog, we have investigated the accepted procedures and methods that can altogether improve the security of programming applications and shield them from likely dangers and weaknesses.
As a matter of some importance, taking on a security-first mentality is fundamental. Security ought to never be a bit of hindsight; it should be coordinated into each step of the product advancement lifecycle. From the underlying plan stage to organization and upkeep, security contemplation ought to be at the very front of navigation.
A vital part of building secure programming is keeping strong and cutting-edge information on expected dangers and assault vectors. This requires consistent schooling and preparation for designers and colleagues to remain informed about the most recent security patterns and best practices. Customary security reviews and code surveys can assist with recognizing weaknesses from the get-go in the improvement cycle, forestalling likely adventures from here on out.
Employing secure coding practices is another fundamental aspect of building secure software. Using secure libraries and systems, input approval, and appropriate mistakes taking care of can forestall normal weaknesses, for example, SQL infusion, cross-site prearranging (XSS), and cushion spills over.
Executing solid verification and approval components is basic to shield delicate information and control admittance to different application assets. Multifaceted verification (MFA) and job-based admittance control (RBAC) are amazing assets in such a manner.
Past secure coding, encryption assumes an urgent part in safeguarding information both still and on the way. Utilizing industry-standard encryption algorithms and implementing secure communication protocols like HTTPS can thwart eavesdropping and data tampering.
Software updates and patches are not to be neglected. Keeping software components and dependencies up-to-date is essential for staying ahead of potential vulnerabilities and exploits. Regularly monitoring security advisories and promptly applying updates can prevent known vulnerabilities from being exploited.
Furthermore, adopting the principle of the least privilege is crucial in limiting potential damage in case of a breach. Giving users and components only the permissions they strictly require can minimize the impact of a security incident.
Finally, cultivating a culture of safety mindfulness among all partners is vital to building secure programming. Everybody engaged with the product improvement process, from engineers to directors, ought to focus on security and work cooperatively to make a versatile and secure programming environment.
All in all, building secure programming is not a one-time task yet a continuous responsibility. It requires dedication, vigilance, and a proactive approach to identify and mitigate potential risks continuously. By following the accepted procedures and methods illustrated in this blog, programming engineers and associations can brace their applications against dangers, guaranteeing the security and trust of their clients in a consistently advancing computerized scene. Keep in mind, the expense of a security break far offsets the interest in developing secure programming starting from the earliest stage. Thus, we should embrace security as a fundamental piece of our product improvement excursion and make ready for a more secure and stronger computerized future.
Recent Stories
500k Customer Have
Build a stunning site today.
We help our clients succeed by creating brand identities.
Get a Quote