Navigating the IoT Maze: Architecture, Security, and Data Mastery

The Internet of Things (IoT) has brought about a profound transformation in how we engage with technology. It has interconnected ordinary objects with the internet, empowering them to gather and share data. This technological revolution is making a significant impact across various sectors, including manufacturing, healthcare, and smart homes. This interconnection is accompanied by a number of challenges, including those pertaining to architecture design, security, and data processing. The complex IoT app design, considerable security issues, and suggested data handling procedures will all be covered in this blog post. A new era of connectedness has been ushered in by the Internet of Things (IoT), in which commonplace things are interconnected and capable of communicating with one another and the cloud. IoT applications have become integral to various industries, from smart homes to industrial automation. A robust IoT app architecture is crucial to harness the potential of this technology efficiently. In this blog post, we will explore the key components and considerations of IoT app architecture.
Understanding IoT App Architecture
IoT app architecture is the structural design that underpins the entire IoT ecosystem. It dictates how devices communicate, how data is processed, and how applications provide meaningful insights. To comprehend IoT app architecture fully, let's dissect its primary components:
1. Device Layer
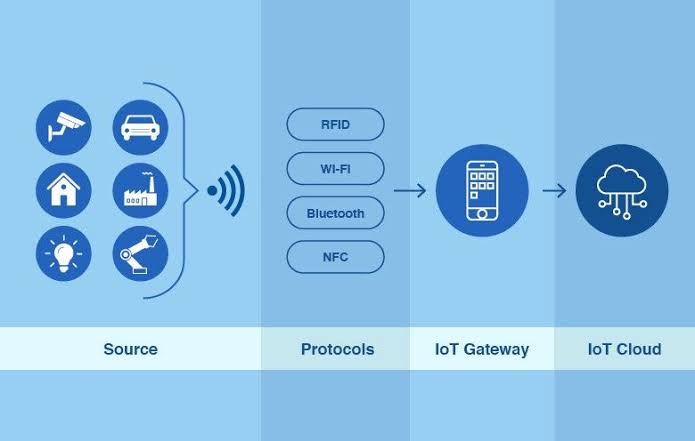
The gadgets themselves are the heart of any IoT system. These gadgets are in charge of gathering information and carrying out tasks. They frequently have sensors and actuators. In a smart home, they may be something as straightforward as temperature sensors, or in an industrial setting, they might be something as complicated as machinery. To ensure an adaptable and scalable design, communication protocols for multiple devices must be standardized.
2. Communication Protocols
IoT devices rely on various communication protocols to transmit data to the central system and interact with other devices. Common protocols include MQTT, CoAP, and HTTP. Things like device capabilities, available bandwidth, and battery consumption affect the protocol chosen. The protocol that is best suited for your specific use case must be chosen in order to increase efficiency and minimize latency.
3. Data Ingestion and Processing
Once data is collected from IoT devices, it needs to be ingested and processed. This can be achieved through cloud-based platforms or edge computing resources. Scalable options for data intake and processing are provided by cloud platforms like AWS IoT, Azure IoT, and Google Cloud IoT. Contrarily, edge computing enables data processing to take place nearer to the devices, lowering latency and enabling real-time replies.
4. Application Layer
The application layer is where the magic happens – IoT data is analyzed, insights are generated, and actions are taken. This layer may encompass various components, including web and mobile applications, APIs, and analytics engines. A successful IoT implementation depends on designing user-friendly applications that can handle enormous volumes of data quickly.
5. Reliability and Scalability
As your IoT ecosystem grows, scalability becomes a pressing concern. A well-designed architecture should allow for the inclusion of additional hardware and data sources without necessitating a significant redesign. In order to guarantee system availability in the event of hardware failures or other disturbances, redundancy methods should also be in place.
Architectural Considerations
While understanding the core components is essential, it's equally important to consider several architectural considerations when designing an IoT application:
1. Security
Security is a paramount concern in IoT. The interconnected nature of devices and data makes IoT systems vulnerable to various threats. Implement strong device authentication, data encryption, and access controls to safeguard your IoT infrastructure.
2. Data Storage
IoT generates vast amounts of data. Choose appropriate storage solutions, such as databases or data lakes, based on your data requirements. Real-time processing may demand databases capable of handling high-velocity data streams, while historical analysis could benefit from data warehousing.
3. Data Processing
Effective data processing is crucial for deriving meaningful insights from IoT data. Consider using analytics tools and machine learning algorithms to extract valuable information. This can include predictive maintenance, anomaly detection, and optimization of operations.
4. Data Visualization
Presenting IoT data in a human-readable format is essential for decision-making. Utilize data visualization techniques to create dashboards and reports that convey insights effectively to stakeholders.
5. Data Governance and Compliance
IoT data often contains sensitive information. Ensure compliance with data protection regulations, such as GDPR or HIPAA, by implementing data anonymization, encryption, and access controls.
IoT app architecture forms the foundation of any successful IoT implementation. It defines how devices communicate, data is processed, and insights are delivered to end-users. To build an effective IoT app architecture, one must carefully consider the device layer, communication protocols, data processing, scalability, and redundancy. Additionally, architectural considerations like security, data storage, data processing, data visualization, and compliance play pivotal roles in the overall success of IoT applications. As IoT continues to evolve and expand into new domains, a well-designed architecture becomes increasingly essential to unlock its full potential while ensuring data integrity, security, and compliance. By embracing best practices in IoT app architecture, organizations can position themselves to thrive in the era of the Internet of Things.
Future Guarding: A Comprehensive Glance at IoT App Security
From smart homes to industrial automation, the Internet of Things (IoT) has changed how we engage with technology. But security is a major worry that comes with connectivity. IoT devices are vulnerable to a variety of attacks, and flaws can have serious repercussions. We will examine the intricacies of IoT app security in this blog article, outlining significant difficulties and recommended safeguards for your IoT ecosystem.
Understanding IoT App Security
IoT app security encompasses a comprehensive set of practices, protocols, and strategies designed to safeguard IoT devices, networks, and the data they generate. Unlike traditional computing devices, IoT devices often have limited computational resources and may be distributed across various locations. Consequently, securing IoT apps requires a multifaceted approach.
Key Challenges in IoT App Security
Before diving into best practices, let's understand the primary challenges associated with IoT app security:
1. Device Diversity
IoT comprises a wide variety of devices, from sensors and actuators to sophisticated industrial equipment. And it is difficult to implement a standardized security approach, since each device may have unique features, software and security mechanisms.
2. Resource barriers
Numerous IoT devices only have a small amount of processing power, memory, and storage. Due to this restriction, it is challenging to incorporate effective security measures without compromising device performance, such as encryption or strong authentication.
3. Firmware Updates
Keeping IoT device firmware up to date is crucial for addressing vulnerabilities and improving security. However, remote firmware updates can be complex and introduce security risks if not implemented correctly.
4. Network Vulnerabilities
IoT devices often communicate wirelessly, exposing them to network-based attacks. Weak encryption, unsecured network connections, and insufficient access controls can leave devices vulnerable to intruders.
5. Data Privacy
A large amount of data is collected by IoT devices and these collected data may include sensitive information also. Therefore, it is a difficult task to ensure that the collected data is handled and stored securely since it navigates through various systems and networks.
Best Practices for IoT App Security
To mitigate the challenges and risks associated with IoT app security, organizations should adopt best practices that encompass device security, network security, data security, and continuous monitoring.
1. Device Security
Device Authentication and Authorization: Implement strong authentication mechanisms to ensure that only authorized devices can connect to your IoT network. Use device certificates or tokens and define access controls based on the principle of least privilege.
Secure Boot and Firmware Integrity: Ensure that devices boot securely and that their firmware is tamper-proof. This prevents attackers from modifying or replacing device firmware with malicious code.
Regular Firmware Updates: Establish a mechanism for remote device management and firmware updates. Encourage users to keep their devices updated to protect against known vulnerabilities.
2. Network Security
Encryption: information or data should be encrypted both in transit and at rest. Use secure communication protocols (e.g., TLS/SSL) to protect data in transit and implement encryption mechanisms to safeguard data stored on devices and servers.
Network Segmentation: Segment your IoT network from your main corporate network to limit the potential attack surface. Isolation helps contain security breaches and prevents unauthorized access to critical systems.
Firewalls and Intrusion Detection: Employ firewalls and intrusion detection systems to monitor network traffic and identify suspicious activities or unauthorized access attempts.
3. Data Security
Data Encryption: Encrypt sensitive data before transmission and storage. Protect data as it travels between devices and the central system by using end-to-end encryption.
Data Privacy Compliance: Implement data anonymization, encryption, and access restrictions to make sure your IoT application complies with data protection laws like GDPR or HIPAA. Clearly communicate data usage and privacy policies to users.
Secure Data Storage: Store data in secure, well-managed databases or data lakes. To restrict unauthorized access to data, access controls can be implemented.
4. Continuous Monitoring and Incident Response
Security Monitoring: Set up continuous monitoring of your IoT infrastructure to detect anomalies and potential security breaches. This may involve keeping an eye on how devices behave, network activity, and data access habits.
Make a thorough incident response strategy that outlines what to do in the event of a security breach. Make sure your staff is equipped to deal with threats quickly and successfully.
IoT app security is an imperative aspect of the IoT ecosystem. As IoT technology advances and is integrated into more and more economic sectors, protecting devices, networks, and data becomes increasingly crucial. By adhering to best practices and routinely monitoring the IoT environment, organizations may minimize risks, protect sensitive data, and maintain the integrity of their IoT applications. Securing IoT apps is a multifaceted challenge, given the diverse array of devices and the resource barriers they often operate under. However, enterprises can defend their IoT ecosystems against a quickly changing threat landscape by putting in place strong device security measures, securing network traffic, protecting data, and having a well-defined incident response plan in place. By doing this, they can make the most of IoT while protecting users' and devices' privacy.
Mastering the Art of IoT App Data Handling: Best Practices and Considerations
A transformative force, the Internet of Things (IoT) links billions of devices worldwide and generates massive volumes of data. The collection, handling, storing, and upkeep of this data must be carefully considered by IoT application developers. In this blog article, we'll go in-depth on IoT app data handling and examine best practices and factors to keep IoT-generated data managed effectively and securely.
The Complexity of IoT Data Handling
IoT data handling involves managing data from diverse sources, often with varying formats, frequencies, and levels of importance. This complexity requires a well-thought-out strategy to harness the value of this data while addressing challenges such as data volume, data quality, data privacy, and real-time processing.
Best Practices for IoT App Data Handling
To excel in IoT data handling, it's essential to adopt a comprehensive approach. Some of the best practices and considerations are as follows:
1. Data Ingestion and Collection
Data Streaming: IoT data is often generated in real time. Implement data streaming mechanisms to ingest and process data as it's produced. Technologies like Apache Kafka or AWS Kinesis can help manage data streams effectively.
Batch Processing: Consider batch processing to gather and process data in pieces in situations where real-time processing is not essential. For managing massive amounts of data at once, this strategy may be more effective.
Data Validation: Implement data validation checks at the ingestion point to ensure data quality. Verify data integrity, format, and adherence to predefined schemas.
2. Data Storage
Choose the Right Storage Solution: Select appropriate data storage solutions based on the specific requirements of your IoT application. Options include databases, data lakes, and cloud-based storage services.
Time Series Databases: For IoT data, time series databases are particularly valuable. They excel at storing and querying time-stamped data, making them well-suited for sensor data and historical analysis.
Data Partitioning: Implement data partitioning strategies to organize data efficiently, making it easier to query and retrieve. Partitioning by time or device ID is a common approach.
3. Data Quality and Preprocessing
Data Cleaning: IoT data can be noisy and may contain outliers or missing values. Apply data cleaning techniques to enhance data quality and reliability.
Normalization: Normalize data to a common scale or format, especially when dealing with data from diverse sensors or devices. This step can improve the consistency of the analysis.
Data Transformation: Depending on the use case, consider transforming raw data into aggregated or summarized forms. This can reduce storage requirements and simplify analytics.
4. Data Privacy and Security
Encryption: Encrypt IoT data both in transit and at rest to protect it from unauthorized access. Use strong encryption algorithms and protocols.
Access Control: Implement robust access controls to ensure that only authorized users or systems can access sensitive IoT data. A common strategy is role-based access control (RBAC).
Data anonymization: To protect individual identities while still enabling useful analysis, anonymize or pseudonymous sensitive data where data privacy is an issue.
5. Data Analytics and Insights
Machine Learning: Leverage machine learning algorithms to extract valuable insights from IoT data. This can include predictive maintenance, anomaly detection, and optimization of operations.
Real-Time Analytics: For applications that require immediate action, implement real-time analytics to detect and respond to events as they happen.
6. Data Visualization and Reporting
Dashboards: Create intuitive dashboards and visualization tools to present IoT data in a user-friendly manner. These tools should enable users to interact with and understand the data effectively.
Alerts: Implement alerting systems that notify stakeholders when specific events or anomalies occur. These alerts can be crucial for timely decision-making.
7. Data Lifecycle Management
Data Retention Policies: Establish data retention policies in order to control the lifecycle of IoT data. Establish the appropriate retention periods for data, as well as when it should be archived and when it can be safely removed.
Data Archiving: For historical data that is no longer actively used but must be retained for compliance or reference purposes, consider archiving it to lower-cost storage.
IoT data handling is a pivotal aspect of building successful IoT applications. A well-structured strategy that includes data input, storage, preprocessing, privacy, security, analytics, visualization, and lifecycle management is needed to manage the data produced by a variety of devices and sensors effectively. Organizations can properly utilize the IoT by adhering to best practices and thoroughly examining the particular difficulties this technology presents. By assuring data integrity, privacy, and regulatory compliance, they can gain insightful knowledge, increase operational effectiveness, and make wise decisions. For businesses and industries wishing to prosper in the IoT era, understanding the art of IoT data management is not only a competitive advantage; it's a requirement.
Seamless Connectivity: Mastering MQTT and CoAP in IoT Integration
Integration of MQTT and CoAP in IoT
Integrating MQTT and CoAP in an IoT ecosystem involves leveraging the strengths of each protocol to build a cohesive communication framework. Here are some scenarios where this integration can be valuable:
1. Bridging MQTT and CoAP Networks
In cases where MQTT and CoAP devices coexist, gateways or bridges can be used to enable communication between the two networks. These bridges convert messages from one protocol to another, ensuring seamless data exchange.
2. IoT Edge Devices
IoT edge devices often have varying capabilities and resource constraints. By offering support for both MQTT and CoAP, edge devices can communicate effectively with a wide range of other devices, regardless of the chosen protocol.
3. Cloud Integration
When IoT data is sent to the cloud, MQTT and CoAP can be used to ensure compatibility with various cloud-based services. This enables organizations to harness the power of both protocols in their data processing and analytics pipelines.
4. IoT Platforms
IoT platforms and middleware often support both MQTT and CoAP, allowing developers to choose the protocol that best suits their use case. This flexibility ensures that IoT applications can efficiently communicate with diverse devices.
The integration of MQTT and CoAP in IoT ecosystems is a testament to the adaptability and versatility of these protocols. While CoAP is a great option for devices with little resources because of its lightweight and RESTful nature, MQTT shines in real-time data transfer and control applications. Organizations can create reliable and interoperable IoT solutions that enable effective data exchange, communication, and real-time decision-making by seamlessly integrating various protocols. MQTT and CoAP are essential tools that span the gap between devices in the ever-evolving IoT ecosystem, enabling the interconnected world we foresee.
Despite the enormous revolutionary potential of the Internet of Things (IoT), it's important to be aware of the difficulties it poses, notably in the areas of architectural design, security, and data processing. Critical components including the device layer, data processing, communication protocols, and scalability must be included in an efficient IoT app architecture. Incorporating device authentication, encryption, firmware updates, network segmentation, and monitoring, security must be given top importance. Finally, effective data handling involves ingestion, storage, quality control, privacy measures, analytics, and visualization. Addressing these crucial issues will be necessary as IoT develops further in order to realize its full potential while reducing dangers and guaranteeing data integrity and privacy. Organizations can use best practices in architecture, security, and data management to provide a solid basis for their IoT applications. They will be able to thrive in the connected world of the future because of this.
Recent Stories
500k Customer Have
Build a stunning site today.
We help our clients succeed by creating brand identities.
Get a Quote