Ensuring App Security in the Development Process

Application security must be emphasized above all else, since technology is currently influencing every aspect of our daily lives. The exponential growth of cyber risks and an increase in the number of malicious parties means that developers need to consider security at each step of their development process. The implementation of comprehensive safety measures from the beginning of the development phase through deployment and on to achieving success phases are necessary for preserving system integrity, safeguarding sensitive data, and protecting user privacy. Because of this, a preventative approach that smoothly incorporates safety considerations into every phase of application development must be implemented. Developers that appreciate this way of approaching issues may minimize risks, gain consumers' trust, while safeguarding the integrity of the digital ecosystem as a whole.
The Importance of App Security
In the current digital environment, the significance of app security cannot be emphasized. App security is crucial for the reasons listed below:
- Numerous programs manage sensitive user data, including financial information, login passwords, and personal data. App security measures are essential to keeping sensitive data safe from loss, alteration, or unauthorized access.
- Preserving User Trust: People expect programs to be reliable and safe. One security lapse might seriously erode users' trust in the app, which could seriously harm the company's or the programmers' reputation.
- Preventing Financial Losses: Financial losses may arise from fraud, money theft, or legal obligations brought on by security breach violations. App security purchases can assist in averting these monetary losses and safeguarding the company's earnings.
- Corporate Continuity: Security incidents can cause financial losses and reputational harm by disrupting corporate operations. Examples of these incidents include data breaches and attack-related outages. Features for app security help to ensure business continuity by lessening the possibility of such disasters.
- Safeguarding Intellectual Property: To prevent theft, illegal access, and reverse engineering, businesses that develop proprietary software or applications need to give app security first priority.
- Expanding Competitive edge: You can have a big advantage over rivals if you have a good reputation in the industry for security and dependability. Companies that put an emphasis on app security stand a better chance of drawing in and keeping clients who respect the security and privacy of their data.
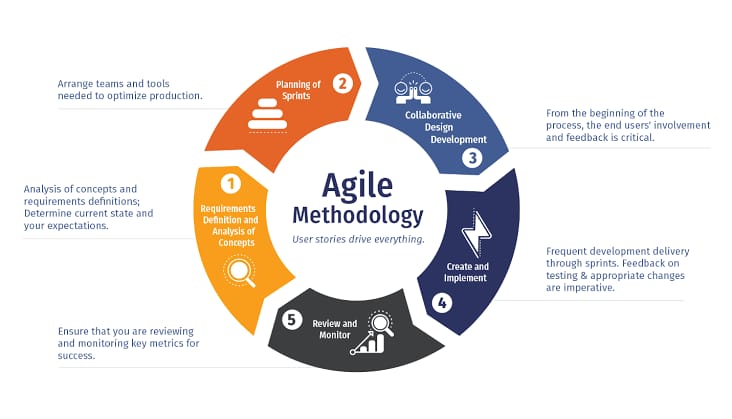
Key Principles of App Security
- Secure Design: During the application development lifecycle's design stage, security ought to be incorporated. This includes developing threat models, spotting any dangers, and putting in place suitable security measures.
- It is recommended that developers follow secure coding practices to protect against common vulnerabilities. This includes using secure libraries and frameworks, handling errors properly, encoding output, and validating input.
- Authorization and Authentication: To make sure users are approved and have the appropriate access permissions to resources, use strong authentication procedures.
- Use encryption to safeguard sensitive data when transporting and storing it to avoid unwanted access. This includes storing data using encryption methods and utilizing safe protocols for communication, such HTTPS.
- Regular updates and patch management: Apply security updates and patches on time to maintain the software and its dependencies current. If external libraries' or components' vulnerabilities are not quickly fixed, attackers may take advantage of them.
- Perform regular security testing, including penetration testing, vulnerability scanning, and code reviews, to identify and address security issues before they become serious.
- Reaction and Event Surveillance: Implement procedures to promptly detect and handle security issues. As part of this, incident response procedures must be put into action, system logs must be monitored, and suspicious activity must be examined.
In conclusion, sustaining confidence, safeguarding user data, and assuring the ongoing operation of businesses all depend on app security. A proactive approach to security can help developers reduce risks and create more resilient and secure systems. Proactive security measures include secure design, secure coding methods, authentication, encryption, and frequent testing.
Best Practices for App Security
To safeguard private information, uphold user confidence, and reduce the possibility of security lapses, it is imperative to put best practices for app security into effect. Here are some key best practices for app security:
- Verify user identities via multi-factor authentication (MFA) or other strong authentication techniques for secure authentication and authorization. Make sure that users are authorized to access the app's resources by implementing role-based access control, or RBAC.
- Robust encryption mechanisms must be utilized to protect confidential information both during transmission and storage. To encrypt any data stored on the device or in server-side databases, connect the application to servers using HTTPS/TLS.
- Preventing injection risks such as SQL injection, cross-site scripting (XSS), and command injection requires often cleaning and validating user inputs. Employ output encoding and parameterized searches to reduce these hazards.
- Secure Coding approaches: Use secure coding approaches to minimize vulnerabilities in the codebase. This entails minimizing buffer overflows and other memory-related problems by eliminating hardcoded passwords, validating input data, and utilizing secure authentication libraries.
- Patch management and upgrades: Make absolutely certain that the most latest updates and patches for security are applied to the application itself and all of its dependencies. To minimize risks, regularly check third-party software and hardware components for vulnerabilities and alerts regarding security. If found, fix them right away.
- Servers, databases, and other components should be configured securely to reduce attack surfaces. Limit access to critical resources, utilize strong passwords and encryption keys, turn off unnecessary services and features, and follow the least privilege principle.
- Make use of secure connection protocols like HTTPS/TLS to safeguard data transmitted between servers and apps. Cert pinning ensures the authenticity of server certificates by thwarting man-in-the-middle (MITM) attacks.
- Protect user sessions against hijacking and session fixation threats by implementing secure session management techniques. Enforce session timeouts, use secure session tokens, and, following authentication, regenerate session identifiers.
- Implementing appropriate error handling will allow you to log errors and deliver instructive messages while protecting private data. Make sure that sensitive data is not logged needlessly when logging security-related events and abnormalities for monitoring and incident response purposes.
- Conduct routine security testing, including penetration testing, vulnerability scanning, and code reviews, in order to find and fix security flaws. enlist the help of impartial reviewers and security specialists to thoroughly evaluate the app's security posture.
- Incident Response strategy: Establish and sustain an incident response strategy for successfully dealing with security-related issues. Create protocols for identifying, containing, removing, and recovering from incidents. Additionally, specify who is responsible for what and establish channels of communication.
- User Awareness and Education: Among other security best practices, educate users on how to identify frauds like phishing, create strong passwords, and connect safely. Clients should be advised to remain alert for potential dangers and given clear instructions on how to report security issues.
Using these app security best practices will help developers and companies produce more dependable and secure apps that protect user data, maintain trust, and reduce the possibility of security issues and assaults.
Addressing User Feedback and Bug Fixes
For an application to remain secure and of high quality, it is essential to respond to user comments and implement issue patches. Here's a structured approach to effectively handle user feedback and address bug fixes:
- Gather Customer input: There are a number of ways to get input from users, such as through social networking platforms, app store reviews, customer service questions, and feedback forms within the app. Urge people to report problems and offer enhancement suggestions.
- Setting Priorities for Feedback and Bugs: Review user-submitted feedback and bug reports, ranking them according to important business priorities, severity, and influence on users. Classify your concerns according to priority by using labels such as vital, high, medium, and low.
- Developing an App to Track Bugs: Install a bug tracking system or make use of project management tools like GitHub Issues, Trello, or JIRA to keep an eye on and track reported defects and enhancement requests. Developers should be assigned assignments, and you should monitor the completion of feature and problem fixes.
- Research and Reproduce Issues: To determine the root causes and aggravating factors, investigate reported issues by reproducing them in a controlled setting. Accumulate pertinent data, including error messages, screenshots, logs, and instructions for successfully reproducing the bug.
- Resolve Issues and Apply Improvements: Using the priority criteria as a guide, devise fixes for issues that have been reported and apply desired improvements. Assure the quality, stability, and security of the repairs and additions by adhering to best practices for testing, coding, and code review.
- Test Fixes and Enhancements: Thoroughly test bug fixes and enhancements in a testing environment to verify that the issues have been resolved effectively and new features function as expected. Perform regression testing to ensure that the changes do not introduce new bugs or regressions.
- Release Updates: Package bug fixes and enhancements into software updates or patches and release them to users through app stores or software distribution channels. To educate users about the updates' modifications and enhancements, provide release notes or changelogs.
- Interact with Users: Update users on the status of issues that have been reported as well as the development of enhancements and bug solutions. Give prompt updates and notifications about the status of software updates and the fixing of identified defects.
- Input on Fixes: After bug fixes and additions are deployed, get user input to make sure the problems have been successfully fixed and the changes live up to user expectations. Urge people to report any problems or concerns that they still have and to offer their opinion.
- Constant better: Examine bug reports and user comments to find trends, underlying problems, and areas that could be used better. Improve the quality of your products, expedite development processes, and prioritize future development activities by making better use of this data.
These procedures help developers and organizations prioritize and fix reported defects, respond to user feedback efficiently, and continuously enhance the apps' quality, security, and user experience. Maintaining the competitiveness and commercial success of the program depends on this iterative process of gathering input, addressing bugs, and implementing enhancements.
Finally, given the state of the digital world today, making sure apps are secure during development is not a choice—it is a need. Developers need to stay alert and aggressive in resolving security issues as technology develops and cyber threats change. Developers may minimize risks, guard against intrusions, and preserve user information and organizational integrity by incorporating security measures from the beginning. Encouraging security also gives users confidence, which encourages loyalty and trust in the apps they use. As we move forward, let us embrace a culture of security-first development, recognizing that safeguarding our digital infrastructure is a collective responsibility that ultimately benefits us all.
Recent Stories
500k Customer Have
Build a stunning site today.
We help our clients succeed by creating brand identities.
Get a Quote